The first step in Apple’s device management process is to connect the device to Jamf Pro, which then sends out controlled tasks, such as performing app installs, system updates, remote locks, remote wipes, and so on. However, all of these tasks are based on the device being in a controlled state. Once a task fails or is on hold, the client may be out of control, but of course, it cannot be ruled out that the client is offline. The following are common anomalies:
- Remote commands issued through Jamf Pro do not take effect.
- Deploying an application from the App Store via Jamf Pro or Self Service does not work.
- Opening a Self Service reports an error or a package installation task within a Self Service fails.
- A new or modified Configuration Profile does not take effect on the client.
- Policy tasks for installing software, executing scripts, or updating Inventory are not executed on the client.
So, how do we go about making a judgement on the client’s control state in such cases? This is the recommended process:
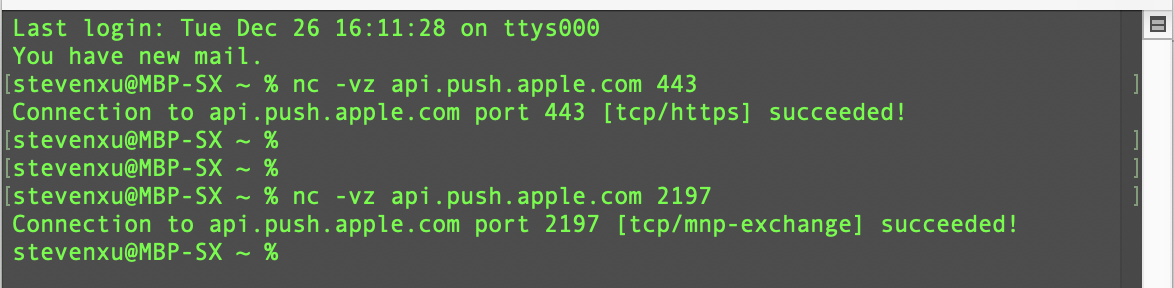
Step 1: Make sure that the client is properly networked at this point and can communicate properly with the Jamf Pro server and Apple Push Message Services (APNs).
1. The macOS client can open the Jamf Pro server’s URL or another website and execute the command to determine whether communication with the APNs is normal.
nc -vz api.push.apple.com 443
nc -vz api.push.apple.com 2197
2. The iOS client can open the web site of jamf pro server or other web sites to make sure the networking is normal.
3. Try restarting the macOS or iOS client.
Step 2: Confirm the online status of the device in Jamf Pro.
1. macOS client can check the last check-in, last Inventory update, last enrollment, and MDM Profile Expiration Date time to confirm whether there is any abnormality.
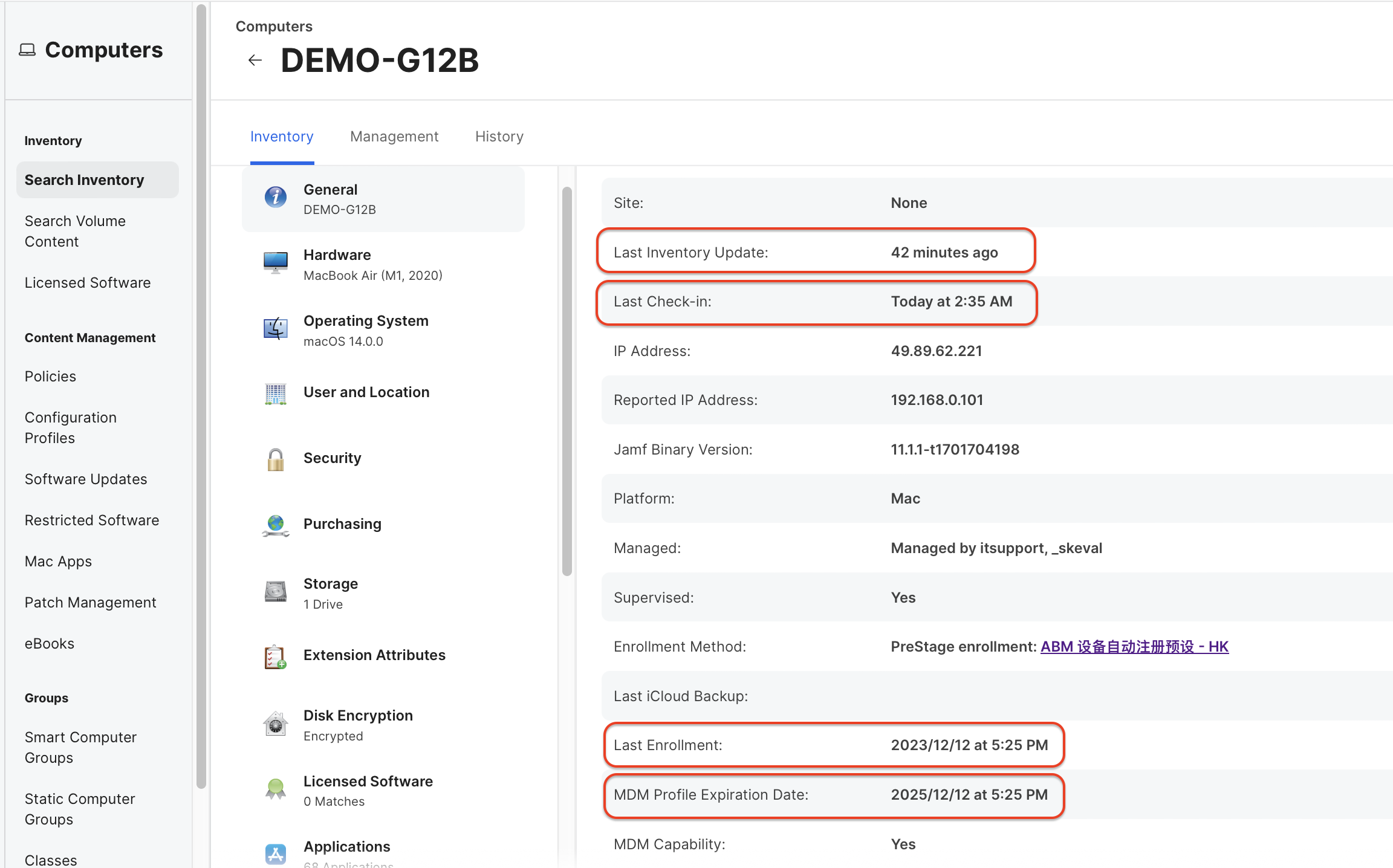
The last check-in is more frequent, defaulting to around 15-20 minutes when the device is online, this frequency can be adjusted in Jamf Pro Settings > Computer Management > Check-In Settings.
The last Inventory update defaults to once a week, and the frequency can be adjusted by going to Computers > Policies > Inventory Update.
MDM Profile Expiration Date is the Last Enrollment time plus 2 years by default, which is the validity period of the MDM client certificate. If this certificate is not renewed in time and expires, the client will not be able to communicate with APNs, and all remote commands, profile issuance, App Store App Push, etc. based on APNs will not be executed successfully.
2. iOS client can view last Inventory update, last enrollment, MDM Profile Expiration Date.
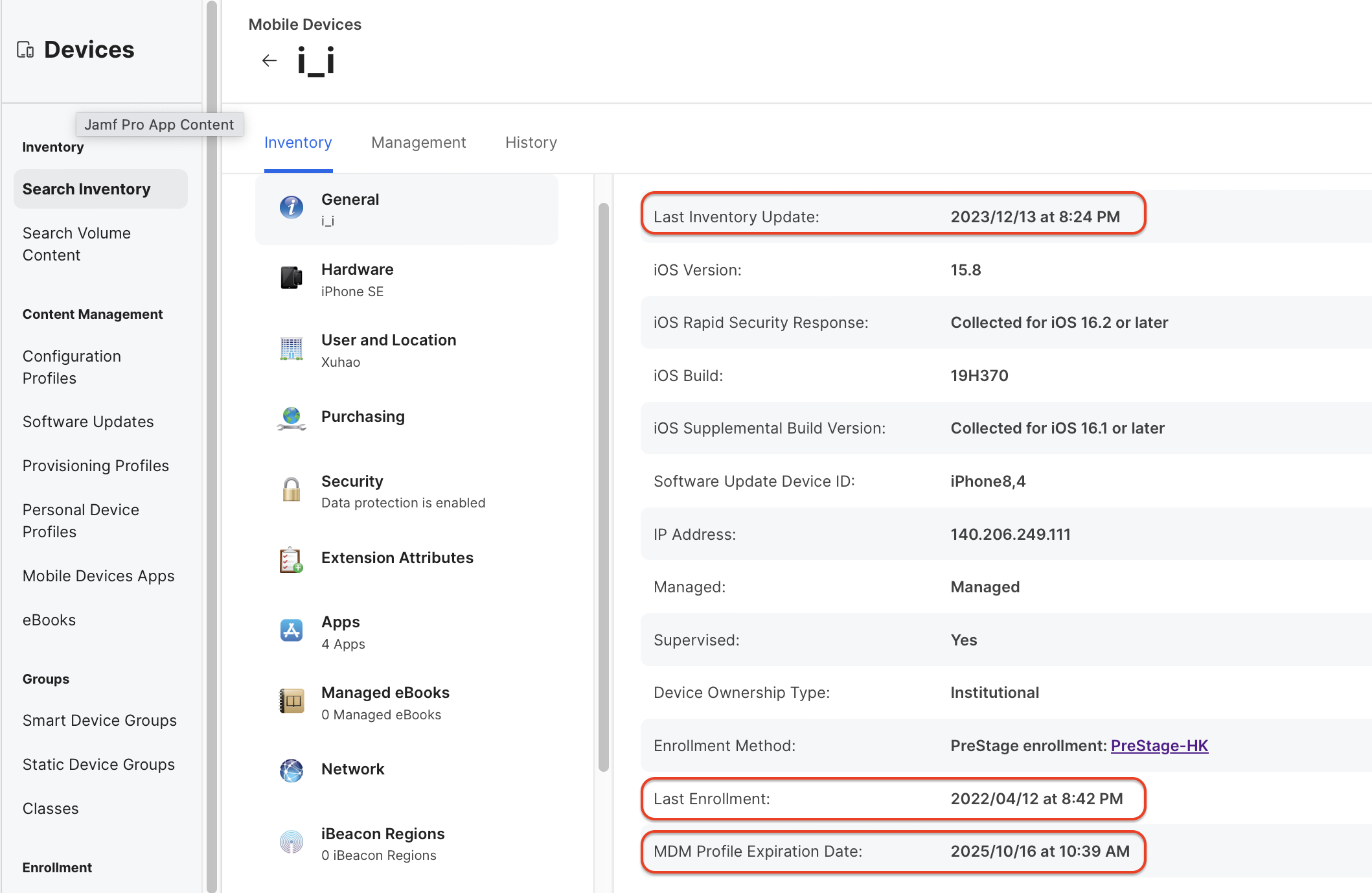
The last Inventory update defaults to a maximum frequency of once per day.
MDM Profile Expiration Date Same as macOS client.
From the above time information, you can basically judge whether the device status is abnormal or not. For example, if the device has been online for more than 3 weeks since the last check-in, or the last Inventory update has been over 2 months since the last Inventory update, or the MDM Profile Expiration Date has expired, it means that the device is basically out of control.
Step 3. Further confirm the device management and control status in the client.
1. Jamf management macOS client is based on Jamf Agent and Apple MDM management framework, so you can start from these two aspects.
1.1 Confirm Jamf Agent
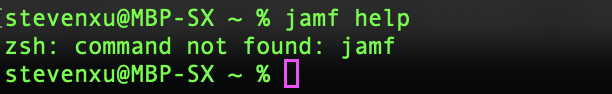
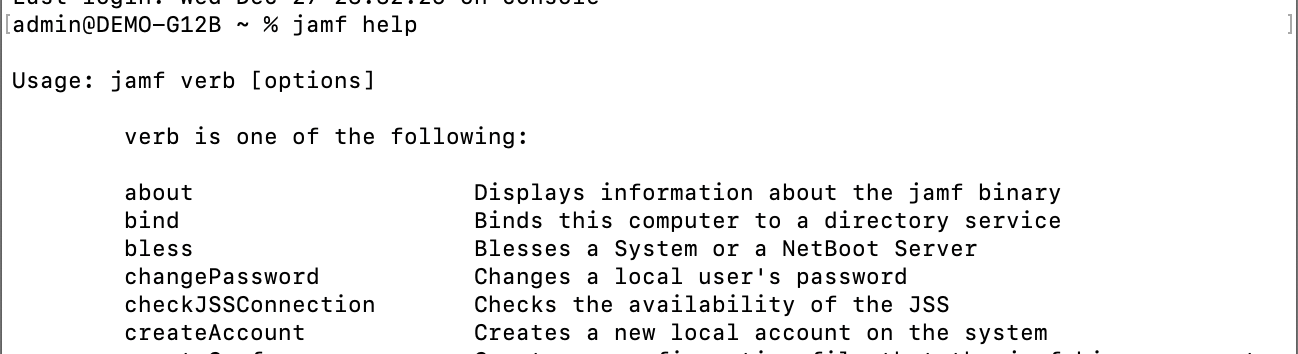
1.1.1 To confirm the existence of Jamf Agent, you can execute the terminal command: jamf help
If you encounter a command not found: jamf error, it means that the jamf binary has not been installed successfully or has been deleted, as shown in the following figure.
If you can return the jamf binary usage instructions, it has been successfully installed, as shown below.
1.1.2 After confirming that the jamf binary is available, continue with the other check commands as follows.
Check communication with Jamf Pro Server: jamf checkjssconnection
Update the Jamf Management Framework: sudo jamf manage
Update the client Inventory asset information: sudo jamf recon
Check pending policy: sudo jamf policy
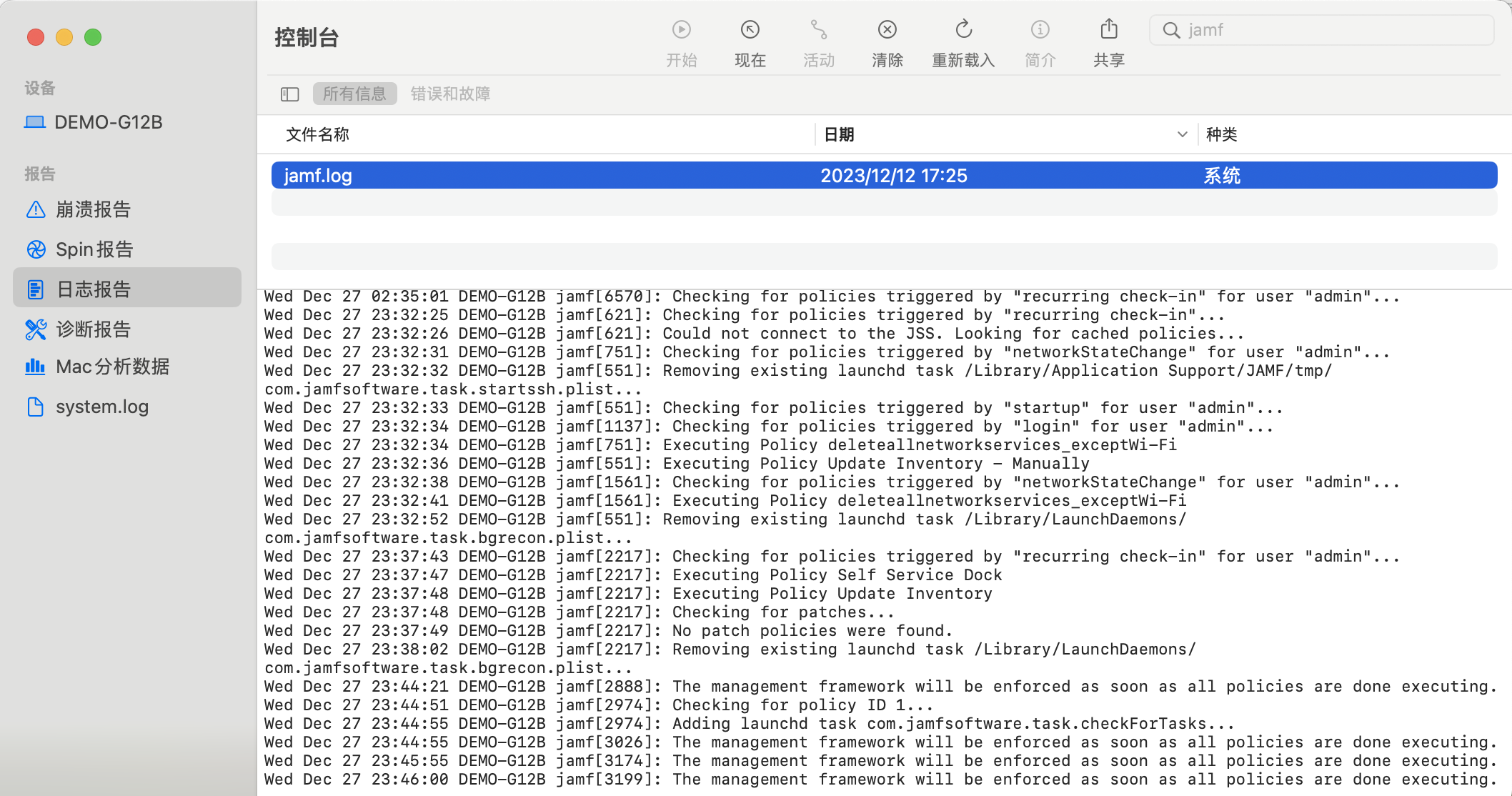
1.1.3 View the /var/log/jamf.log log or open Console.app to view jamf.log and try to find anomalies.
1.2 Confirming the MDM Client Device Identity Certificate
The MDM Client Device Identity Certificate is accomplished by embedding the PKCS#12 profile payload in the enrolment profile when the device is enrolled to the MDM server, which becomes the device’s proof of identity. If this device identity certificate does not exist in the keychain or does not match the one in Jamf Pro, it may be due to the device having performed a Migration Assistant or Certificate Removal operation, which will result in all APNs-based push tasks failing or remaining pending, such as remote commands, profile push updates, app store application installations, and so on.
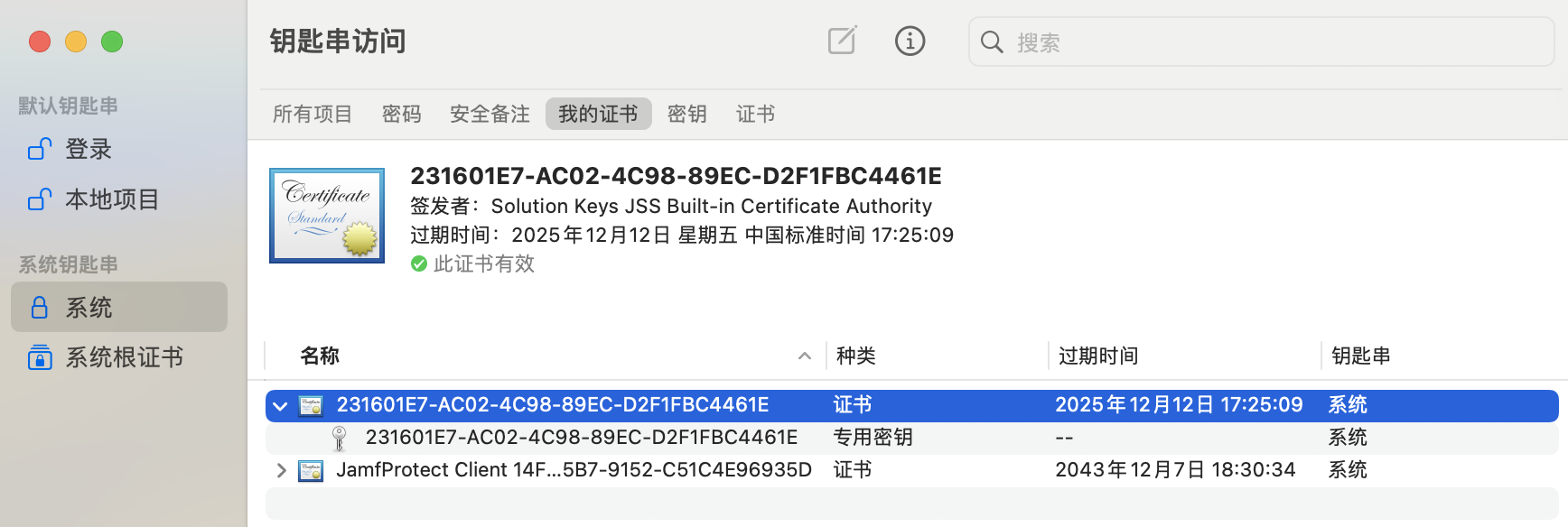
1.2.1 Open the keychain keychain.app, go to System > My Certificates, and verify that the Client ID certificate exists and is still valid, and that it matches the name and validity of the certificate in the Inventory of this device in Jamf Pro.
2. Jamf Management iOS client is completely based on Apple MDM management framework, you can start from these aspects.
2.1 Query whether the MDM profile exists. Settings > General > VPN & Device Management > Mobile Device Management > MDM Profile.
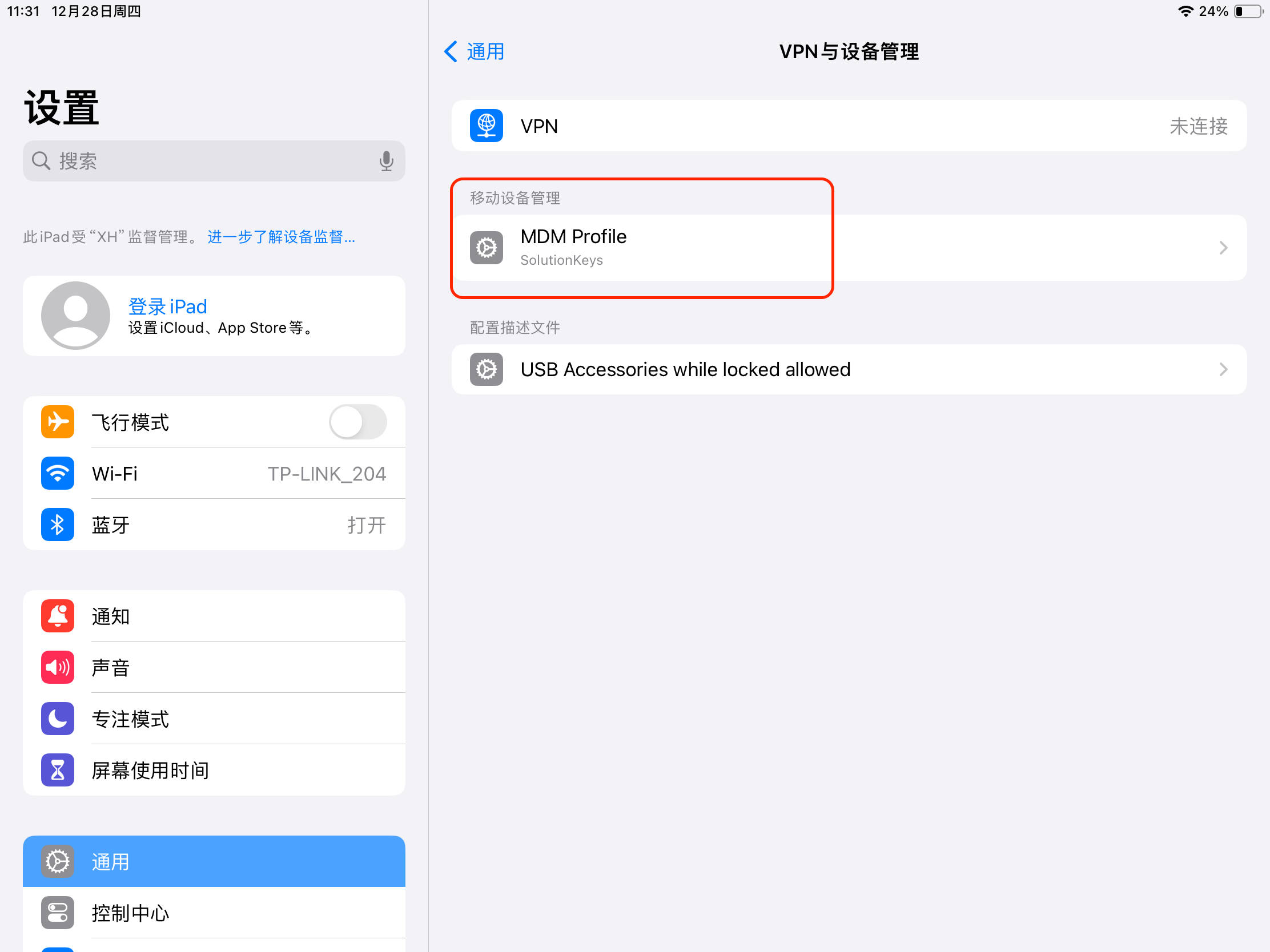
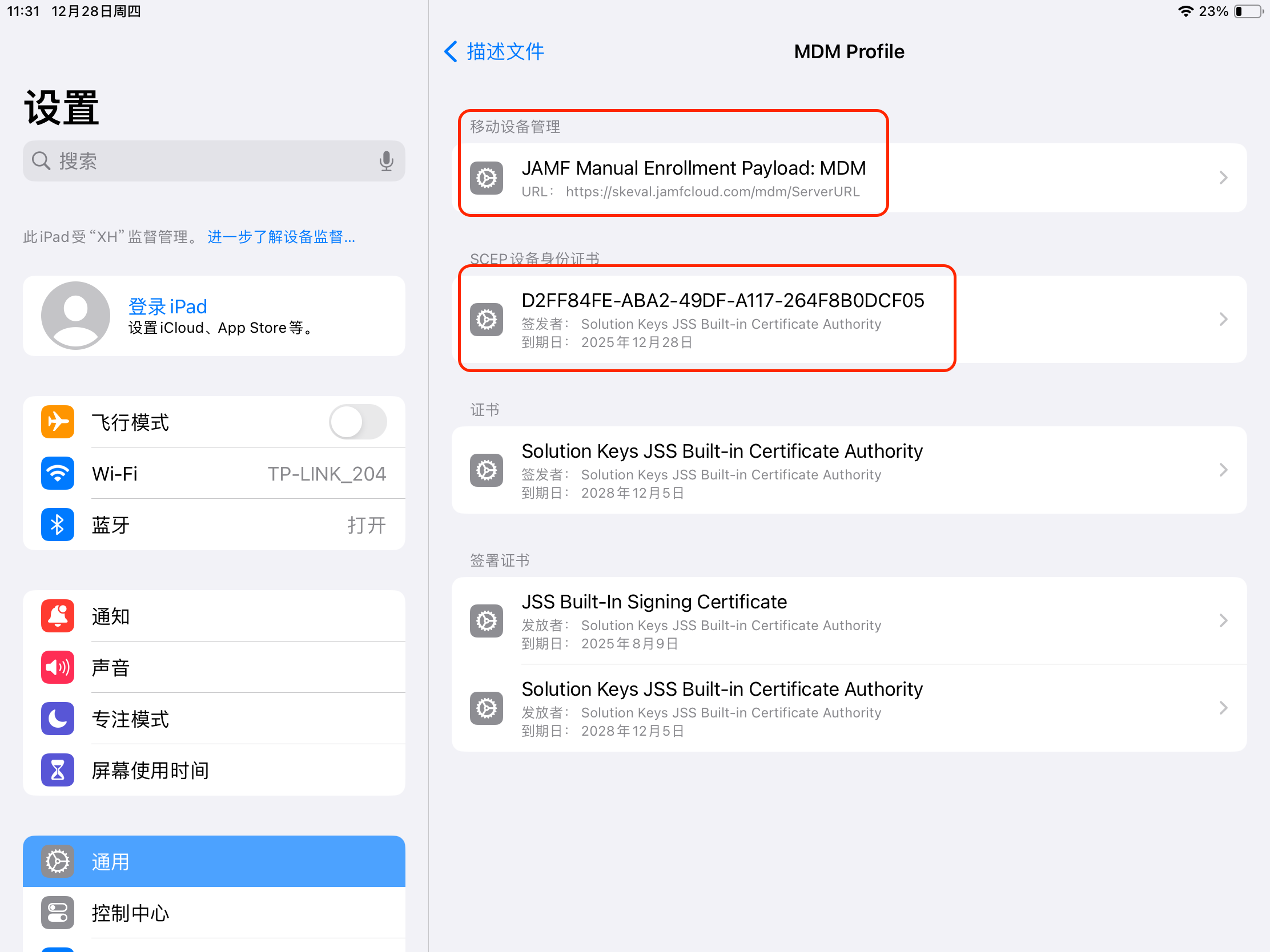
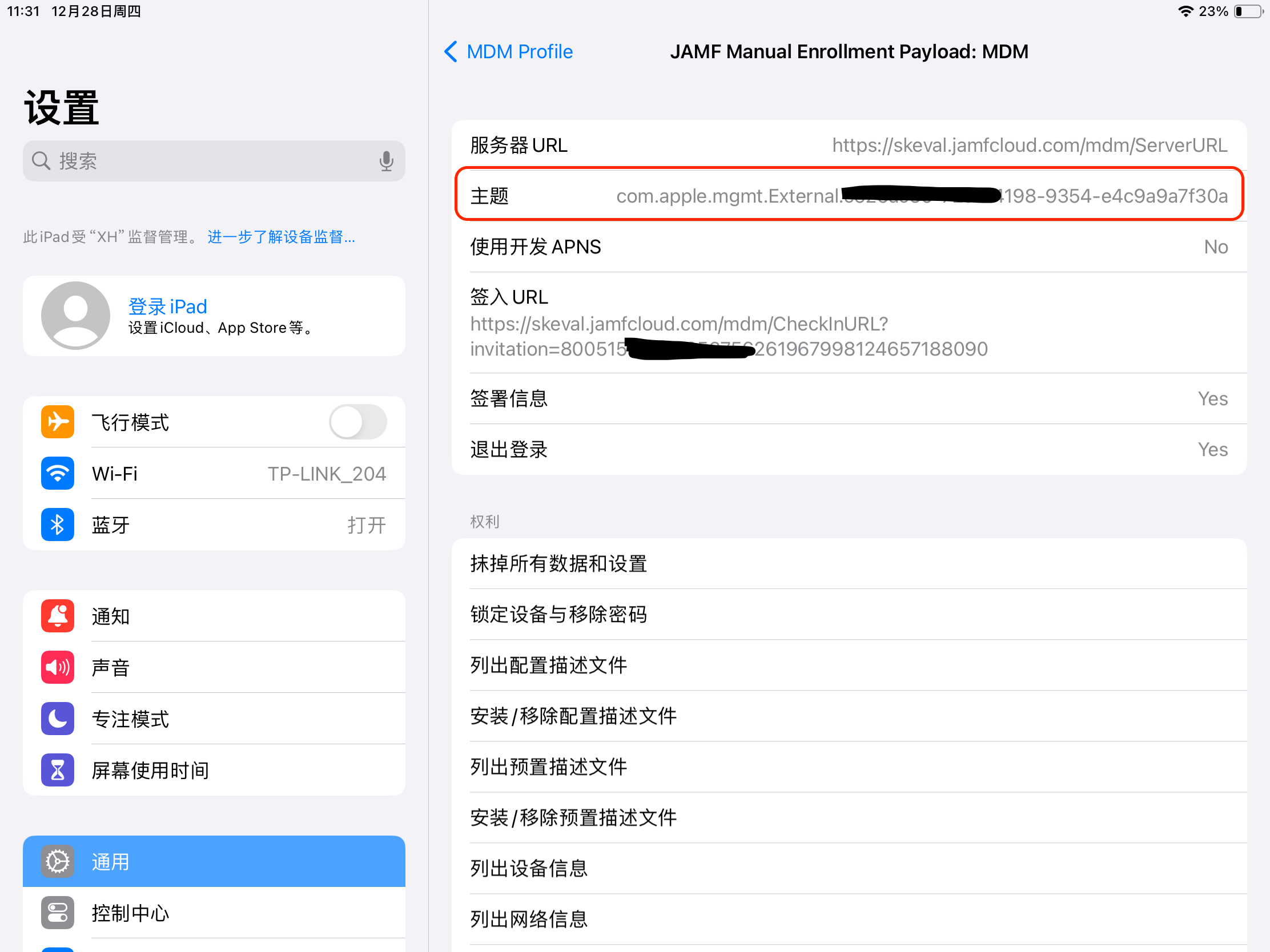
2.2 Verify that the APNs certificate subject within the MDM description file is the same as in Jamf Pro. Settings > General > VPN & Device Management > Mobile Device Management > MDM Profile > Mobile Device Management > Jamf xxx Enrollment Payload: MDM > Subject.
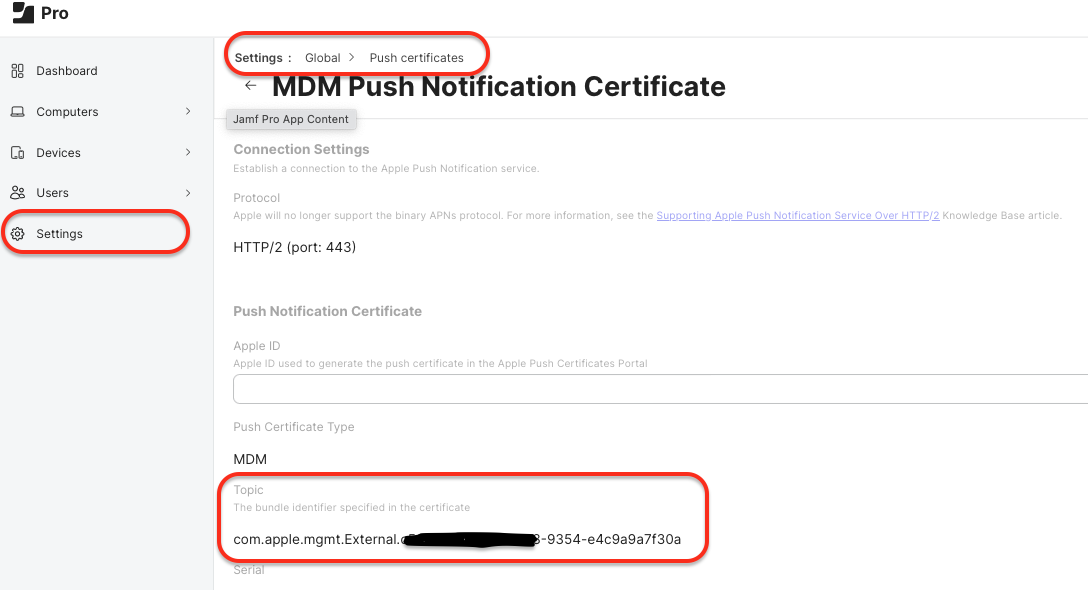
Jamf Pro Settings > Global > Push Certificate > MDM Push Notification Certificate.
2.3 Verify that the device identity certificate matches the certificate in Jamf Pro.
Settings > General > VPN & Device Management > Mobile Device Management > MDM Profile > SCEP Device Identity Certificate
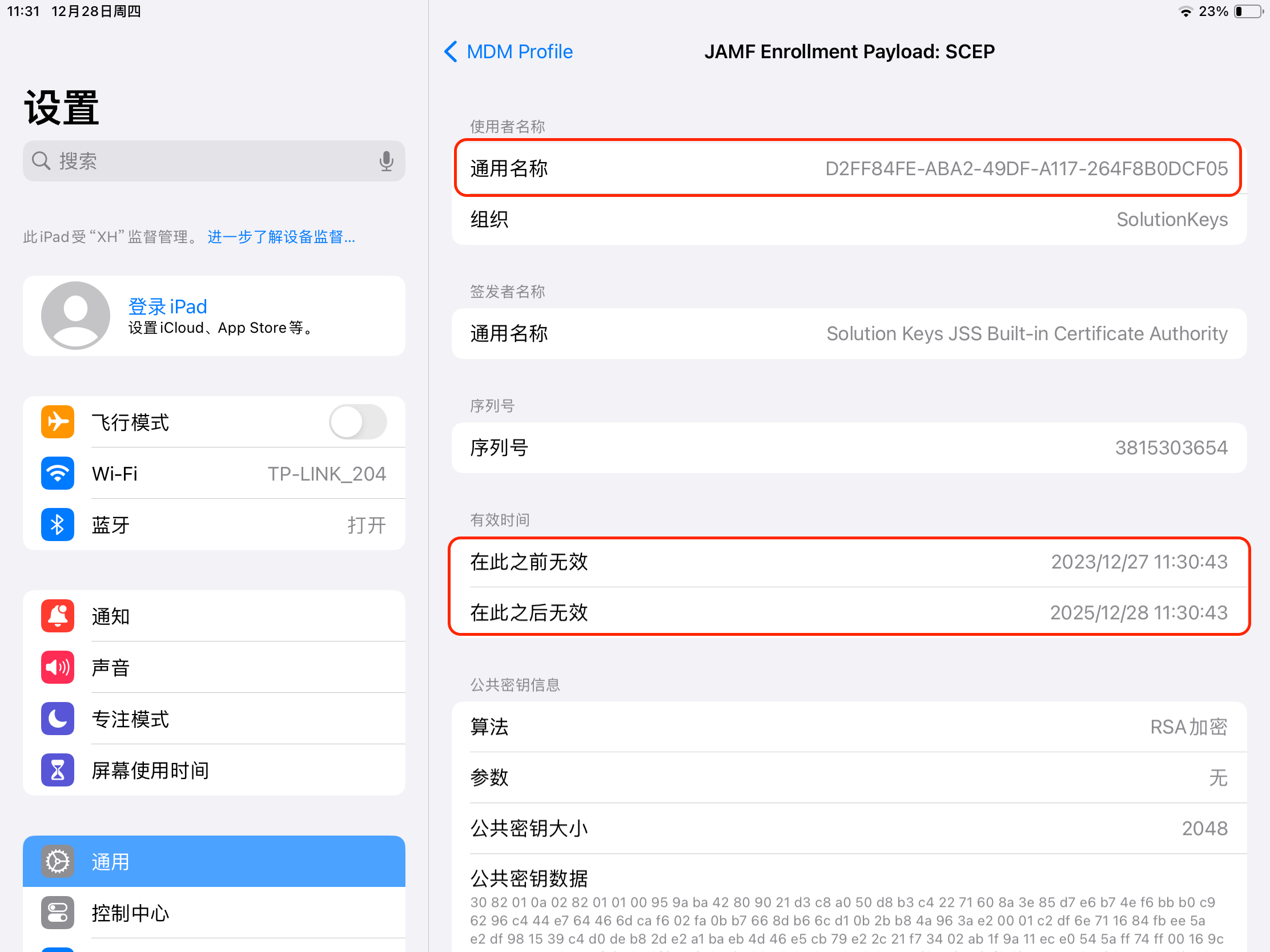
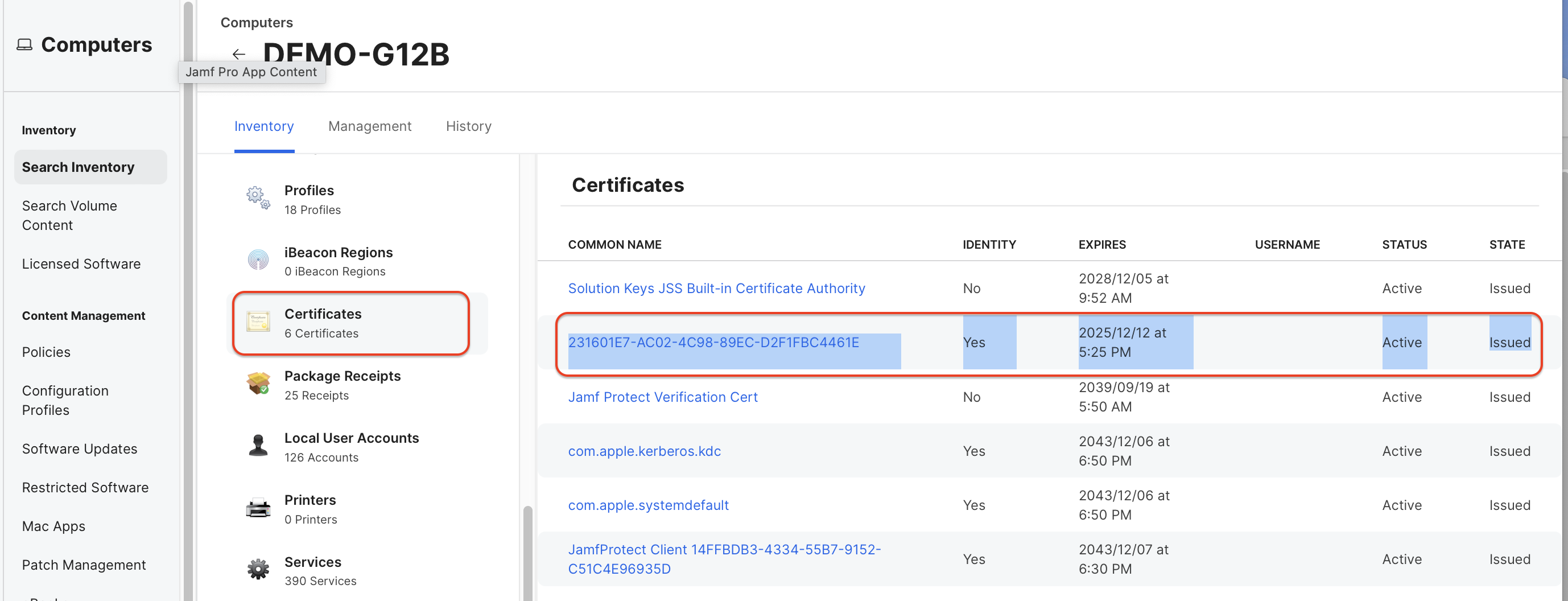
Jamf Pro > Devices > Search Inventory > “Device Name” > Inventory > Certificate.
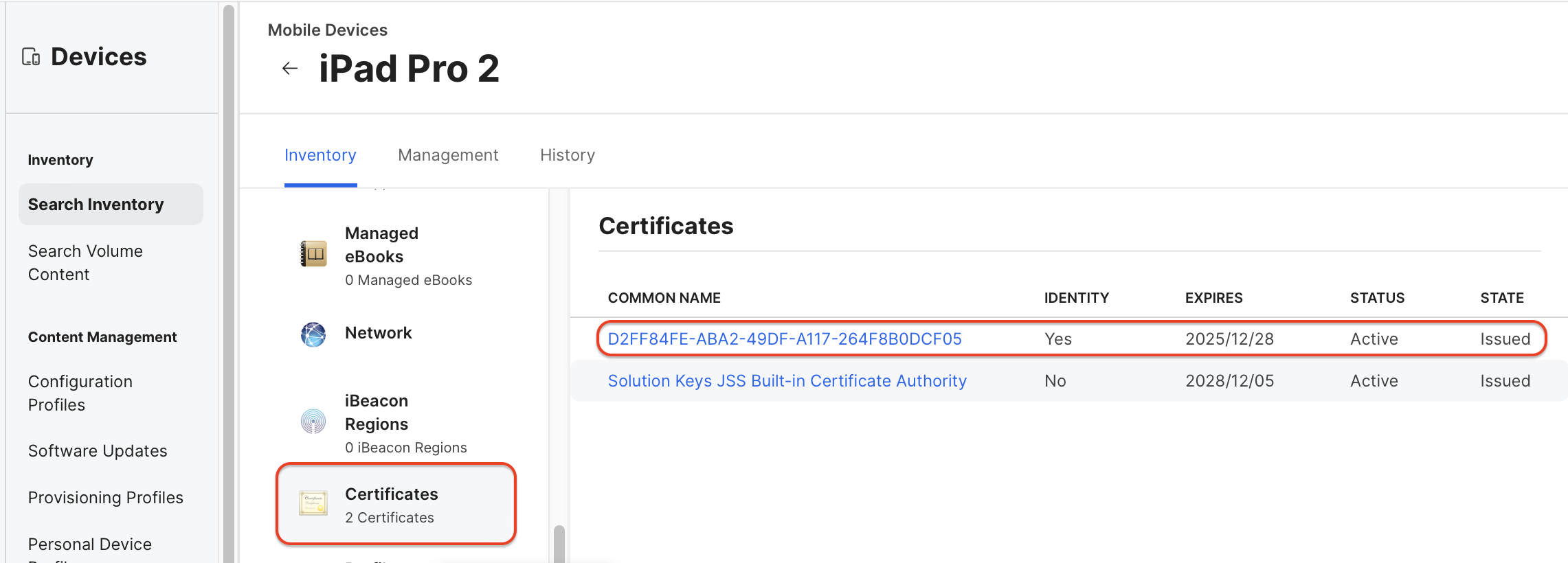
By checking the logs, information, certificates, etc. of Jamf Pro server and client, if there is any abnormal situation as above, re-registering the device is the best and fastest solution.
We hope this will help Jamf Pro administrators to deal with the problem of device de-registration.
If you have any questions, please contact us or send a work order email to help@solutionkeys.com.
